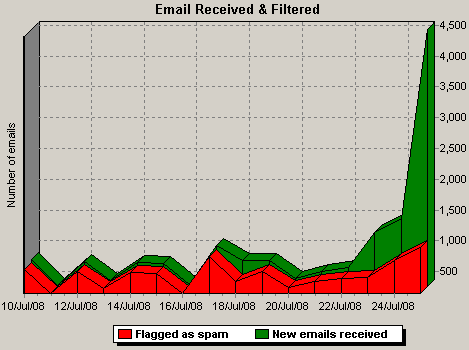
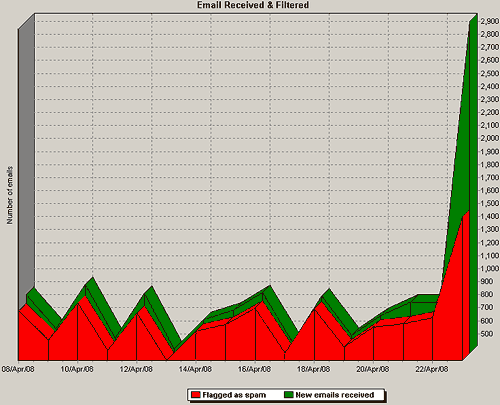
I know what you're wondering. You're wondering how many penis-pill spams I get per hour.
Well, gentle reader, it varies, depending on the time of day, from about six to about fifteen.
Per hour.
For some weeks now, the most popular ones have had subject lines that always contain a name, a word vaguely denoting bigness, and a word vaguely donating a dickish object, in various arrangements.
Some of the words for "big" are particularly entertaining. Actual subject lines I've seen include HoracioObviousFuckstick, BouffantPenisRosetta, and ClarkOverlargeBodypart (overlarge?).
(The penis I've been promised has also been described as "spacious". I'm sure "massive" has been in there, too - though "sturdy" and "fearsome", sadly, remain unused.)
The body of these messages always includes another of the three-word portmanteaux, followed by the URL of a Web site. There are many such sites - calormontes.com, grayskues.com, janeoplane.com, jeroneus.com, junioeres.com, planesjanes.com, razkoesu.com and slopitues.com were all promoted in one day - all registered with nonsense details to Some Dude In China.
All of them currently give you the same site (on, I think, the same physical server), promoting a product allegedly called "VPXL" from a company allegedly called "Express Herbals".
The VPXL/Express Herbals guys are the source of the vast bulk of my dick-pill spam, and I bet they're the source of most of yours, too, if you're not using an airtight spam filter.
(I've got three active e-mail addresses at the moment. The filtering on my iiNet account lets through zero spam but no doubt bounces a few valid messages; I only use it for a couple of mailing lists and occasional personal messages, though, so that's fine. I've also got an old Optus account I hardly ever use for anything, which is almost as well filtered; only a few spams a day get through there. And then there's dan@dansdata.com, messages to which get an "X-Spam-Tests-Failed:" header tacked on by m'verygoodfriends at SecureWebs who host Dan's Data, but are very minimally filtered by them, if they're filtered at all. Hence: Spamvalanche!)
Like the previous fake marijuana spams, the VPXL ones come to you courtesy of a botnet - a huge collection of virus-infected home computers on ordinary Internet accounts, identifiable because the sending IP addresses for the spam vary widely but always belong to some ISP or other that serves the home-user market.
The botnet this time is called Mega-D, and it has the interesting quality that its infected machines almost all seem to be in non-English-speaking countries. (The previous Storm-botnet spam overwhelmingly came from the USA.)
The VPXL dudes now seem to be shifting away from the three-word spams. In one 155-minute period earlier today I received:
One VPXL spam directly promoting http://polierin.com/; it came from a codetel.net.do IP address (Dominican Republic).
One VPXL spam with an "I'm Feeling Lucky" Google link (http://google.com/pagead/iclk?sa=l&ai=acetate&num=137336094&adurl=http://clinrie.com?446) that takes you to the spammers' site, in this case clinrie.com. The spam came from 58.19.232.188, a China Network Communications Group Corporation IP address.
One for jilafen.com from 80.146.114.212, a Deutsche Telekom address.
One for nidegnero.com from 201.19.74.24, a probably-Brazilian IP address.
And another variant, whose body text said "Pls Go ' www.redmehs ' dot com"; redmehs.com is VPXL yet again, registered to Chinese nonsense yet again. This one came from 68.118.233.112, though, which is an IP address belonging to Charter Communications in the USA.
There was exactly one spam that actually mentioned VPXL in the text of the spam - but it was malformed, with no actual link to anywhere you could buy the product. It came from 92.112.20.89, belonging to Ukrtelecom in the Ukraine.
And then there were a couple of the classic three-worders, one from Peru and one from Chile, both promoting zhbvdiaeg.com.
And then there was yet another variant, from a Colombian IP address and promoting http://geocities.com/kathydowns889/, which is a redirector page that sends you to neverwaitons.com, another facade for the Express Herbals server.
The runners-up in the dick-pill spam-flow are the "Canadian Pharmacy" type (the sites are usually subtitled "#1 internet online drugstore"). The most prominent products on these sites are, of course, always erectile dysfunction drugs. Which you almost certainly will not actually receive if you place an order.
In my 155-minute period I got one promoting marquitamontemurrodd.blogspot.com, which redirects to a Canadian Pharmacy site at putwish.com, which is registered to a pile of Chinese nonsense that closely resembles the standard VPXL-domain registration nonsense, leading me to suspect they're related. The spam came from 220.128.197.130, some Taiwanese mail server.
And then there was one that directly promoted canocaw.com, "Target Pharmacy", registered to more Chinese nonsense and also billed as "#1 Online Pharmacy Store", and looking much the same as the "Canadian" version. The sender was 84.108.33.6, belonging to Bezeq International in Israel.
Another one promoted tamilacyg.blogspot.com, which redirected to another "Canadian Pharmacy" at pha-cana.com, an unusually comprehensible domain name for these guys. More Chinese rego details; spam sent from 82.54.82.43, Telecom Italia.
And one promoting ruoedi.kiltyale.com, which is "World Pharmacy", which looks a bit different from the Canadian and Target varieties. Kiltyale.com is registered to marginally more real-looking Chinese details than the other pharma-sites, but the spam came from 190.156.83.182 in Colombia, which suggests the Mega-D net again.
And then there was one promoting the entirely genuine-sounding URL http://gbcdelmafhjk.filmplenick.com/?iafhjkxowptygzchcmbcdelm, which is a "Viagra + Cialis" site calling itself "VIP Pharmacy". Filmplenick.com is registered to a US address, so even though this was another spam from a South American IP address, I suspect it's not the same people as "Canadian" and "Target".
And then there was one for www.onthebob.com, a site that's regrettably down right now - one of only two pharma-spams whose promoted sites didn't work - and which is registered to pointless details in Brazil rather than China, suggesting that the culprit is different again. The spam came from 60.242.181.54, which is a TPG Internet IP address right here in Australia.
The other complete failure had the subject "Hydrocodone, Vicodin, Phentermin, we are 100% reliable pharmacy retailer cufqev21ph", and advertised gop.uhthclrenewed.com, which is down (so not quite 100%, I guess). Actually, the uhthclrenewed.com domain isn't even registered as I write this, so spamming about it would appear to be slightly premature. This spam originated from 66.228.248.134, belonging to the gloriously titled "Park Region Mutual Telephone Co. and Otter Tail Telcom" in the USA.
On top of these, I got one ad for pohfrensei.com, selling the entirely non-icky product "WonderCum". This is the VPXL people again; that domain is registered to more Chinese nonsense, and WonderCum and VPXL are often sold - or complained about - on the same sites. This spam came from a BT Total Broadband IP address in the UK, though.
(The VPXL people have also been responsible for "Elite Herbal", "Manster", "ManXL" and the delightfully understated "Megadik".)
There was also one quit-smoking spam advertising something called LiveFree at www.celarpo.com/f/. That's probably unrelated to the dick-pills people; the domain is registered to someone allegedly in the USA, and the spam came from 201.226.17.2, somewhere in South America.
I also got one sad little "RE: February 88% OFF" (the number varies - in one mail check a while ago I got eight different "discounts"...), allegedly from "admin@viagra.com", with a link to a broken redirector. Presumably that's the remnant of an older botnet, still spamming sporadically away with out-of-date info.
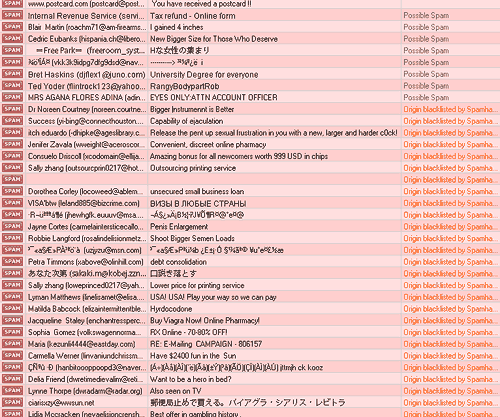
Along with all of the above, and not counting the spams not in English that I couldn't figure out, my 155-minute period netted me nine casino spams (including four copies of "RE ORDER Casino"), six offers of business loans, two counterfeit-watch spams, five counterfeit-other-things spams (four were in Asian character sets, but "Gucci" and "Tiffany" stood out in the headers...), two "offshore printing service" spams (I've been getting those for a while), one fake-lottery spam, two eBay phishes, and exactly one of those magical messages that's nothing but the bare minimum headers needed to get it to you, with no subject, To: line or body.
Yes, I have thought about just redirecting all of my mail through Gmail or something so that I won't smell this constant tide of manure any more - even if all it can do is slap up against my MailWasher deletion queue. I doubt Gmail filtering would be any worse than what I'm doing now - I may be manually scanning over the headers of my mail, but I'm sure I've failed to notice valid mail and deleted it anyway.
But there's a sick fascination to doing it this way.
It's interesting to see the sheer quantity of repeato-spam. You don't get to appreciate the magnitude of the problem - sucking up Internet bandwidth, server power and the money you pay for Internet access - if you hide behind a filter.
The current repeato-spam onslaught is, I think, created by the distributed botnet senders. Botnets are a great way to spam, but they have no way to coordinate their sending lists.
Spammers never prune their mailing lists anyway, and I do know that one should never underestimate the stupidity of spammers, but I think even the dumbest modern mass-mailing software ought to be able to avoid sending the same spam to the same recipient twelve times in one run. If you've got thousands of zombie PCs sending your spam independently, though, it becomes much harder to prevent the same recipient getting (essentially) the same message over and over and over in a short period of time, because none of the individual bots know which other bot has sent which message to which recipient.
This is probably why I got three copies in quick succession of "AGF has an exellent opportunity for you! Australia", plus one "AGF is a smarter way to money! Australia", three "New part time job - good salary in Australia", one "Work with us today - earn money today!", one "AGF company helping individuals in business online" and one "it is your new job possible!". All in the course of, I don't know, maybe three hours.
I suppose someone's dotty email-forwarding great-aunt might think this just meant these people were really really eager to find new employees. But super-repeato-spam like this, and like the three-word dick-pill tirade, ought to have some negative effect on the message's credibility to even the most cretinous of other recipients.
Another attraction of paying (at least a little) attention to incoming crap is that you get to see how much of it, as in this case, resolves to just a very few senders.
If someone found, and dealt with, in one way or another, just the VPXL spammers, the total volume of spam in the world might well drop by a double-digit percentage. It's not often that crime prevention has such a definite monetary payoff; since spam costs the world tens of billions of dollars a year, you could easily save a sum equal to the Gross Domestic Product of an African nation by shutting down just one major spam-group, as long as another didn't rise up to take their place.
And that might well not happen, if we establish just a little deterrent value. First World nations need to crack down on spam more effectively, and Third World nations need to realise that spammers are (a) rich and (b) probably all pudgy and easy to rob, 'cos they spend a lot of time sitting in front of a computer.
Legal prosecution would be good. But I'd settle for standover men.
"I bet that stuff you sell's given you a really big dick. Would you like to keep it?"