Suddenly, I've got a few readers - who are presumably, as is usually the case, representative of a lot more people - complaining about "fake antivirus" malware pop-ups when they visit dansdata.com.
Some people will see crapware pop-ups when they visit any random site, because they installed some crapware in the past, and now it's wedging itself into their browser all the time, showing them porno ads or asking them to install more crapware. (Or it may just be quietly waiting for them to type some interesting-looking usernames and passwords.)
This is not like that. This really does seem to be some actual malware associated directly with dansdata.com.
The only reader who managed to see what the bad ad did in any detail reported that it:
1: Apparently opened a PDF file in the Internet Explorer Adobe Reader plug-in
2: Used some exploit in that to install crapware called "Antivirus Live"
3: Popped up tons of fake system errors and immediately made his life very miserable
Another reader didn't see what the heck actually happened, but swears he never clicked an "OK, install whatever the hell it is you want to install!" button, also received a delicious heaping mouthful of brown and steaming fake antivirus software.
Yet another reader also had the experience that's more normal among drive-by banner-ad crapware-installer victims, which is to say:
1: Reader is peacefully reading one of my pages.
2: Reader clicks on a link to another of my pages.
3: Reader suddenly gets a bunch of terrifying popups about viruses.
4: Reader employs the sure-fire highly technical hacker-neutralisation technique.
5: Reader comes back to computer later, and spends hours on end trying to remove all of the malware that installed itself entirely without reader's knowledge. This can be a huge pain.
(Note that that post is three years out of date, and about me dealing with a really mild crapware problem. I presume that current crapware swims up your urethra and then flicks out a crown of asbestos thorns.)
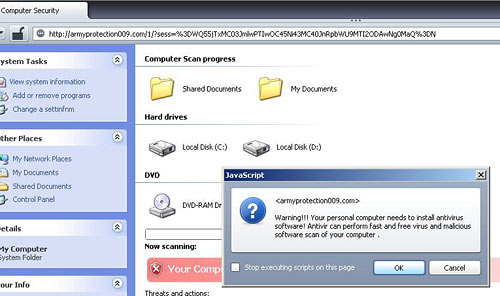
Another reader reported that the bad ad, or whatever the heck it is, tried to redirect to armyprotection009.com, which is on Firefox's "Attack Site" list (and also Chrome's, and I presume recent versions of various other browsers too).
That site's purpose in life...
...seems to be to pretend to be a Windows folder with a scary security warning in it, and get you to click OK to install "Antivir", which may or may not be the same BS malware antivirus as the apparently-installed-via-PDF "Antivirus Live" above.
I don't know for sure what it is, though, because armyprotection009.com is as I write this not resolving to anything any more. (I presume this is another of those weird hosting deals where sites, and the very nameservers that resolve them, come and go like the unlocatable voices of invisible summer insects. It's all very poetic.)
Even if I can find one of the redirected-to sites, that doesn't help much, because I need to know where the nasty redirecting ads are coming from. I presume it's either some exploit on the actual Web server, or an ad being served by one of the two outfits that serve ads to dansdata.com, Burst and Google.
(There are other ads on the site, most notably all the click-here-to-buy ones from Aus PC Market, but they're just a static image and link, not something all rich-media-y being served from somewhere far away.)
I know Burst have "subcontractors" who run ads not entirely under Burst's control; that's caused some scammy ads to show up from time to time, but never any actual malware. I don't know whether Google does a similar subcontracting thing. And it's made even harder to figure out by the way these crap-ads works. You see, like legitimate advertisers who try to avoid advertising the new season's Buicks to people who live in Sweden, crapware-servers serve different things to different IP addresses.
So even if it's a Burst subcontractor - not that I'm saying that it is - that's serving the ad entirely deliberately and not because some server of theirs has been compromised, it's perfectly possible that even if Burst carefully screen every single thing served in their name, they'll never see the malware, because the malware authors have Burst's whole IP range on a "do not serve malware to" list.
(This may fall down when a Burst employee goes home and uses his home ADSL connection to look at some site that runs his company's ads, of course.)
So now I'm e-mailing Burst and Google and my Web hosts. And with any luck, this post will crowdsource some more info.
I know there are people reading this who have a computer full of sacrificial virtual machines, and/or serious TCP/IP-and-Web chops. If any of you would like to dangle an unsuspecting virtual PC's Internet Explorer 6 in front of dansdata.com for a few force-refreshes, or (more importantly) trace where the hell this shit is actually coming from, then please, please do.