A spammer has just used my e-mail address as the return address for a good-sized run of spam. Gee, it's fun when that happens.
In case this is all new to you: There is nothing verified about the From: or Reply-To: lines in an e-mail. A sender can put whatever they like in there. Spammers do this as a matter of course, generally picking some address out of the same list to which they're sending the spam, or picking something relevant-sounding like admin@viagra.com or bigmoney@amazingsupercasino.biz.
It seems, at least, that Internet users are now savvy enough that they don't send outraged messages to these bogus reply addresses any more. Or maybe the people who're prone to do that are all now just behind good enough spam filters that they never get to see that "I" sent them 300 porn spams today. So that's a relief.
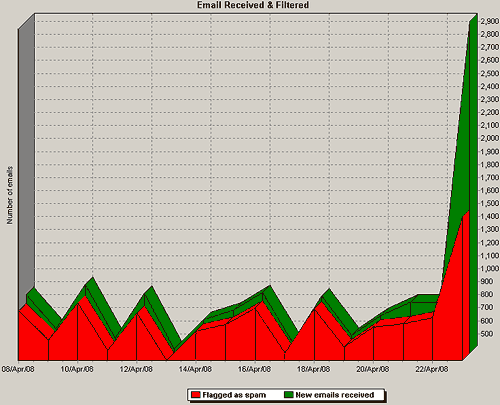
But I've still ended up with the thick end of three thousand "backscatter" bounce messages from moronic mail servers that don't check to see whether, perchance, incoming obvious spam might just possibly not have a genuine reply address. Nope, they (a) accept the mail, even though they could tell instantly that it's for an address that doesn't exist, and (b) then cheerfully send an error e-mail. And they send that error e-mail to the Reply-To address, because how could the Reply-To for "Hot replica watches from 2008" or "ivagra ciails" possibly not be real!?
What mail servers should do in this situation is check the recipient before they accept the message, and reject message delivery if the recipient does not exist. Then an error gets sent directly to the sending mail server.
Backscatter will still exist even if every mail server got this right, but it'd be restricted to far rarer things like "I'm out of the office" messages, and other kinds of autoresponder systems.
The backscatter bounce flow seems to have slacked off a bit, now; it's down to about five bounces a minute. And it's not terribly onerous for me to MailWash all of those bounces out of existence. Actually filtering backscatter bounces is a bit tricky - in essence, you probably do want to receive bounces from messages you actually sent, and backscatter bounces look very much the same - but manually deleting them with some sort of header-preview tool like MailWasher is no big deal.
Mixed in among the thousands of bounces, though, were a few other things, one of which I'd never seen before.
For every few hundred nonexistent-address errors, you see, there are a few "please confirm your subscription" messages. Those are from mailing list servers that treat anything sent to subscribe@dumblist.example.org as a subscribe request, even if it's an ad for porn or watches or pharmaceuticals.
This does no real harm - it's just another darn message in among the bounces - unless the list is one of the old-style ones that don't require a subscribe confirmation.
Here's a new one, though. This spammer sucessfully UNSUBSCRIBED me from a mailing list!
I'm a subscriber to Jakob Nielsen's Alertbox list, which is administered by Sparklist. It's normal for mailing list unsubscribe requests to not require a confirmation, and clearly Sparklist don't spam-filter unsubscribe messages. So when the spammer sent some piece of crap or other to leave-alertbox@laser.sparklist.com, "from" dan@dansdata.com, it cheerfully unsubscribed me.
My actual Alertbox e-mails have a different unsubscribe address, leave-alertbox-[seven-digit-number]Y@laser.sparklist.com, which probably isn't in any spammer's database, and would be unlikely to be generated randomly either (yes, spammers send spam to aaaa@example.org, aaab@example.org, aaac@example.org...). But I just tried unsubscribing by e-mailing plain old leave-alertbox@laser.sparklist.com, and it worked just fine. So I reckon that's the button the spammer pressed.
I just subscribed to Alertbox again, so there's no real harm done there, either. But it was a pure fluke that I noticed the lone "Alertbox unsubscribe confirmation" message in the middle of the thousands of bounces and other messages. It didn't even come from the same address as the subscribe confirmation messages, so whitelisting that address wouldn't have helped me. If this had been some mailing list that was essential for my job, or something, I could have missed a few issues before I noticed.
Thanks again, spammers! You're doing a heck of a job!
23 April 2008 at 6:58 pm
>What mail servers should do in this situation is check the recipient before they accept the message, and reject message delivery if the recipient does not exist. Then an error gets sent directly to the sending mail server.
It's very difficult to do this if you're a secondary MX - especially when the people you're secondary for demand that you don't filter their mail, they have specially tailored this and that... *sigh*
24 April 2008 at 10:38 am
Actually the recipient check method is fouled as well since spammers figured out, "Hey! This is a great way to test what addresses ARE valid here!" They then proceed to run a list of recipients 400 miles long through the system, including sometimes using the randomly generated names.
So there is the tar pitting method where every "RCPT TO" request gets either 1 second added or an n+1 system to get progressively slower. This stops the mail address harvesting since it isn't feasible in the lifespan of the computer it is running on, but this generates issues and errors for real mail in the corporate world (and mail lists) and for some reason runs the machine into the rails with many connections that I have not had answered (at least on Exchange 2003).
Having said all this, it is pretty damned stupid to have the server setup to do this. I end up explaining this process and why the users at work are receiving these mailings for things they have not sent... repeatedly.
24 April 2008 at 5:15 pm
Not only do you have to wade through the volumes of backscatter, but imagine the headaches for the poor list Owners and Moderators who also have to deal with it, too. For every error that gets bounced to you, there's a high likelihood that one goes to the Owner as well. If a list's address is targetted as a recipient, and it's a moderated type that requires a real human to approve posts, the Moderators then have to troll through them all to weed out the chaff from the grain.
Of course, there's a special place in my heart for spammers who use the list's address as the origin...that way the Site Admin where the mailing list manager is hosted gets to share in the pain, too.
Oh, and for the record, a well-behaved non-brain-dead mail server should never be sending bounces to the address that appears in the From: or Reply-To: fields. They should be using the Return-Path: field (which is functionally equivalent to what's seen in the MAIL FROM command of the SMTP transaction, but could possibly be forged as well). You can argue that if it's a null return-path '' then From: or Reply-To: is valid, but in this case the server should be smart enough to just drop it on the floor.
25 April 2008 at 10:46 pm
If everyone would start using Sender Protected Framework, it would solve a lot of these issues.
26 April 2008 at 3:39 am
I had this happen too - I was checking email ~2 weeks ago, and my normal 60 messages per 10 hour load suddenly shot up to ~800 messages... Lots of fun for a home email account.
I saw bounceback and "delayed delivery" emails for at least 5 days afterwards.
27 April 2008 at 1:04 am
There's been a second, smaller run today, giving me several hundred more bounces.
I'm also intrigued by the a new run of German pharmacy spams, all of which have, thanks to the usual letter-duplication obfuscation techniques, the subject line "Internetttapoooootheke".
("Apotheke" is German for "pharmacy". I can only presume that an "apoooootheke" is a place where certain mail-order DVDs with a rather specialised audience are produced.)
3 May 2008 at 1:59 am
This used to happen to be on a semi-regular basis, but on a smaller scale. A particularly egregious spamming operation, operating out of Asia, whose database I was in (probably because of my address appearing in the From: fields of usenet posts; this was a while ago) appeared at that time to have a practice of randomly grabbing a fresh address from their database for each message sent, or at least for each SMTP connection. So my address, being in their database, got used as a From: field several times an hour, continuously. I also got quite a bit of spam directly from them, so I was able to piece together a reasonable amount of information about their operation. They migrated to a fresh IP address every few hours, usually within the same Class A network (either that or they kept a full Class A of mail-sending computers busy, *shudder*, but I think rather that they were migrating across addresses as a filter-thwarting mechanism), but periodically (after weeks or months) they would move to a new Class A. Sometimes they had control of three or four Class-A IP ranges simultaneously, always within APNIC space. They made no attempt to couple email addresses to language, and they sent spam in a number of languages, but it was *mostly* Chinese (or gb2312 at any rate) and English. Mostly.
Since I don't read chinese, I used to filter more than half my spam based on character set alone. Then the botnet spammers came along, and unicode, and the filtering has become much more difficult these days.
I am hoping to eventually move to a system wherein I create a distinct email address to give to each sender (or, at least, a distinct address for each situation in which I am giving out my address), and then when the spammers get one address I can just change that address without changing all the others.