I'm finally shifting my password collection out of my previous ultra-secure unencrypted text file and into KeePass. KeePass is a mature open-source password storer which seems quite easy to use, and makes no doghouse-worthy security claims.
Plus, it's nifty.
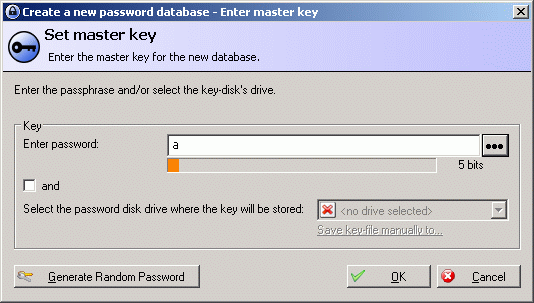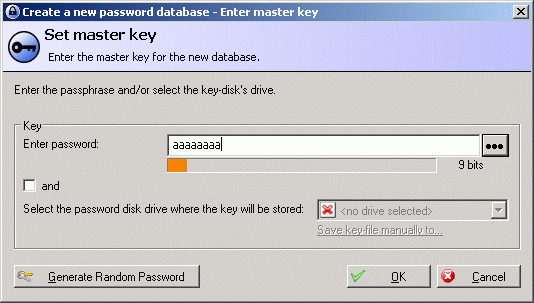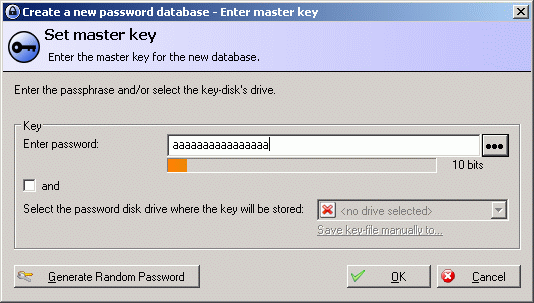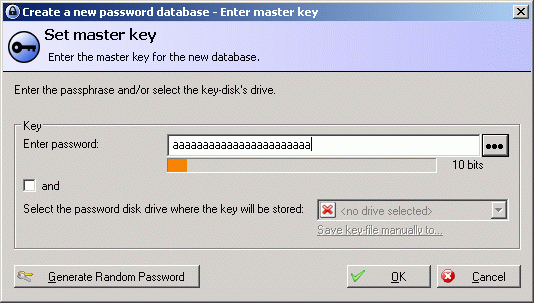
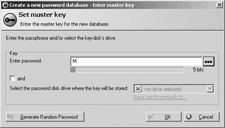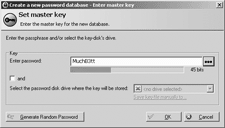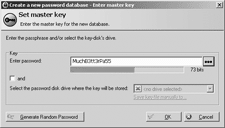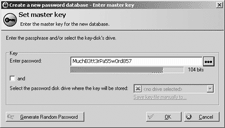
Here, KeePass is showing me that a line of identical characters may be a long password, but it's not a good password.
You get this little dynamically-updating bits-of-entropy graph whenever you enter a password - for the KeePass "vault" itself, or for one of the sites/devices/whatever whose passwords you're keeping safe in KeePass.
This is a really neat way of illustrating the idea of password complexity. It doesn't take into account dictionary attacks, though, which in the modern world are not slowed down much by brilliant tricks l1k3 the u5e of 1337-sp34k. If your password is a dictionary word, then even if you obfuscate it with letter-to-number swaps, it's probably still crackable in minutes, not weeks.
A string of three dictionary words with a few digits on the end, though, is reasonably secure...
...so what KeePass is telling me here (click the image to see the larger-filed original) is fair enough.
To avoid the dictionary-word trap, you can either do this sort of thing - a lot of dictionary words in a "passphrase", or a few words and some numbers - or you can use one of those ludicrous more-or-less genuinely random "T\:;9+jrF:y4+@cf#6'w7z" or "Suy7JOvd" kinds of passwords.
Or you can make up nonsense words. That's what I often do.
If you're trying to crack a password and a dictionary lookup won't help, the length of time it'll take to guess is directly related to the amount of information entropy the password contains. Information entropy is, in brief, an objective measurement of the amount of information something contains.
"Suy7JOvd" is higly memorable, by the standards of true random passwords, but it has only 48 bits of entropy. It is, therefore, feasibly crackable by brute force on a single modern PC in a usefully short time.
"T\:;9+jrF:y4+@cf#6'w7z", on the other hand, has 132 bits, which pushes it well into the "cubic kilometres of sci-fi nanotech" category. For all practical intents and purposes, a password like this one can't be brute-forced. The only way you can hope to crack it (as opposed to just steal it from someone who knows it) is by exploiting some weakness in the cryptographic system being used (to hash the password, or to protect the data to which the password allows access).
Which is all very well, but even "Suy7JOvd" is pretty bloody hard to remember. "T\:;9+jrF:y4+@cf#6"w7z" is ridiculous. Everybody knows that people who're given such passwords just write them down, usually on Post-It notes which they stick to their monitor. Or - if they're especially devious, and very proud of their intelligence - they stick them to the underside of a desk drawer.
Steel door two feet thick, lock utterly unpickable and unforceable... key hidden under the doormat. (Or, if you prefer, trap-door in the floor.)
So - nonsense words.
"Slobodongoo" is a 48 bit password, appears in no dictionary, and is quite easy to remember.
"Grobbynolofroidicality" is 85 bits, which is quite enough for pretty much any purpose. And it's also reasonably memorable, though I recommend you not wander around the office muttering something like that. It's bad security practice to speak your password aloud, and it may also cause your coworkers to take action.
If you're determined to go to 128-bit password strength, which is ample for every single purpose on the planet Earth (unless it's important to you that God not be able to crack your password), then "Seglifromobulgradistalibilitegumentsic" manages it. Inserting capital letters and/or spaces can get the length down - "GorgoBrindyFerguBolishSkuziPlen" and "Mali Colu Snobo Limby Tij WoB" are each 128 bits, too. Punctuation can help a lot - "Eeble frong? Zoiby. Nyoj!" is 128 bits as well.
None of those are, I grant you, particularly easy to remember. But they're easier than "j3JBRGjxYCllgW2s2xccLZB9ww".
And you don't need 128 bits, anyway. 70 or so will do just fine.
"Nerbolica grib" and "Ib? Galoomb!" are both 71.
(If you don't have the kind of brain that comes up with nonsense words easily, or if you're paranoid about some subconscious bias that'll make the nonsense words you make up guessable, there are online nonsense-word - and nonsense-passage - generators that'll do it for you. There's also JabberWordy and NameStation, which make up nonsense-word domain names and sees if they're registered - but you can of course use the words for something else. True Security-Mindset paranoids can make a sentence, each word of which is from a different generator!)
It's not very hard to remember a few of these kinds of passwords. Look at all the people who can remember "Supercallifragilisticexpialidocious", after all. That's a 112-bit word right there - though it's probably in lots of password cracking dictionary files, along with several spelling variations, and is therefore not actually very useful. But you get the idea.
Passphrases can be just as good. The only real problem with them is that they're always significantly longer than an equally secure nonsense-word password, since dictionary attacks mean that a "70-bit" passphrase is not actually as secure as a 70-bit nonsense word, unless your nonsense word turns out to actually be a dictionary word in some language you don't know.
Long passwords also, of course, take longer to type, especially since password boxes that sensibly display asterisks while you're typing make it impossible to tell if you've made a typo until you hit return, get an error, and use some of your profanity allowance.
So go ahead and use passphrases, if you like.
Personally, I'm going to stick with the Flobadob-speak.
23 October 2006 at 4:30 am
Having a hugely long password seems a bit unnecessary. So far as I can tell, there are only three conditions needed for a good pass.
1) 8 or more characters
2) Not in a dictionary
3) 4 character sets
If someone had a password like this:
abcefghi
.. and the attacker knew it was lowercase only, they'd have to run through, at maximum, this many combinations:
(26)^8 = 208,827,064,576
That's crackable within an hour or two depending on the hardware.
But if someone made a pass like this:
aA224$(*
That's:
(10+26+26+10)^8 or thereabouts. Which is about 3000 times harder to crack, or about 2/3 of a year. In any setting where it matter, presumably people are required to change their pass more than once every 8 months.
If you went hogwild with some of the less common special characters, you could likely get by with a 6 digit pass.
23 October 2006 at 5:15 am
Indeed, for the vast majority of cases, if everyone's playing fair, then forty-something bits of password ("aA224$(*" is 44) are more than adequate. Again, nonsense words work nicely here - "PombleboM" is 46 bits.
But there are many factors that can reduce the strength of your password. Encryption weaknesses commonly knock off a few bits, and then there's straightforward stuff like being shoulder-surfed; if the attacker only knows how many characters there are in the password then that won't help him much (unless the fact that it's obviously only four characters is what induced him to try cracking it in the first place...), but if he knows there's a double 2 in it, that helps more.
And it's far from impossible that the next crowd of zombified XP boxes will be running a distributed password cracker for someone. Bingo - processing times divided by a thousand or more, and an unfeasible two year crack becomes an easy 20 hour one.
So there's still good reason to add a few more bits, provided it doesn't make your password uselessly immemorable.
23 October 2006 at 9:37 am
Passphrases of Vogon Poetry can also be somewhat memorable, if you are into that sort of thing. "O freddled gruntbuggly..."
(no I didn't just give away my passwords) :)
23 October 2006 at 10:34 am
I'm a big fan of the long acronym password, which I guess is similar to a passphrase:
pC+A+D2utc!
"press Ctrl + Alt + Del to unlock this computer"
You can use famous quotes, song lyrics, all sorts of stuff.
23 October 2006 at 11:17 am
I use physics equations. I spent a month of back and forth with the Georgia Tech password guesser before I hit on that idea.
By the way, Steganos Locknote is another option for keeping passwords secure. It creates an AES-encrypted file with a single password to access it. The encryption is part of the document so you only have one file to keep up with. You could just copy and paste your entire list. I used to use keepass but I am lazy and it was too much maintenance.
23 October 2006 at 4:43 pm
The number of bits you need for a good password depends on how you're going to use it. Most applications - logging into gmail, say - do not allow massive systematic attempts to crack the passwords. So anything with more than, say, ten bits of entropy is probably enough. Seems like not enough? The way your gmail password is most likely to get cracked, by far, is by you using the same password elsewere, with someone who lets it slip. This is much more of a danger if you use a long, difficult-to-remember one. Alternatively, it can leak when somebody gets a peek into your browser's collection of stored passwords. Anyway, what do you need memorable passwords for if you're storing them? Use some gibberish from /dev/random and copy them every time.
For those rare times you actually *do* need a good password, a dictionary can provide you with a reliable amount of entropy. My /usr/share/dict/words has about 100000 entries, so picking five words really at random gives me a guaranteed 83 bits of entropy. And who can't remember a five-word nonsense phrase? If it's hard, generate eight phrases, pick your favourite, and count on 80 bits.
24 October 2006 at 11:47 am
One bugbear I have about passwords is corporate systems that require users to change them every month, resulting in the entirely predictable "petnamex" password scheme, where x is incremented monthly.
Does anyone have a nice reference to information that could assist in arguments with the corporate security drones about the fact that a rarely changed secure password is vastly superior to a frequently changed predictable password? I always use the example of online banking or ATM PIN numbers (which rarely or never change), but that doesn't seem to be enough.
24 October 2006 at 11:53 pm
One devil of a method for adding complexity to passwords is using non-standard ASCII characters.. like: ╚ or ± .. According to that program just one of those in a password adds 15-20 bits of complexity. Only problem is not all passwords support those fiddly characters.
29 February 2012 at 2:43 pm
Sorry for bumping this (hey.. it's been only ~6 years! lol) but I just had to post this.. so appropriate :)
http://xkcd.com/936/